- 首页
- » 新手园地
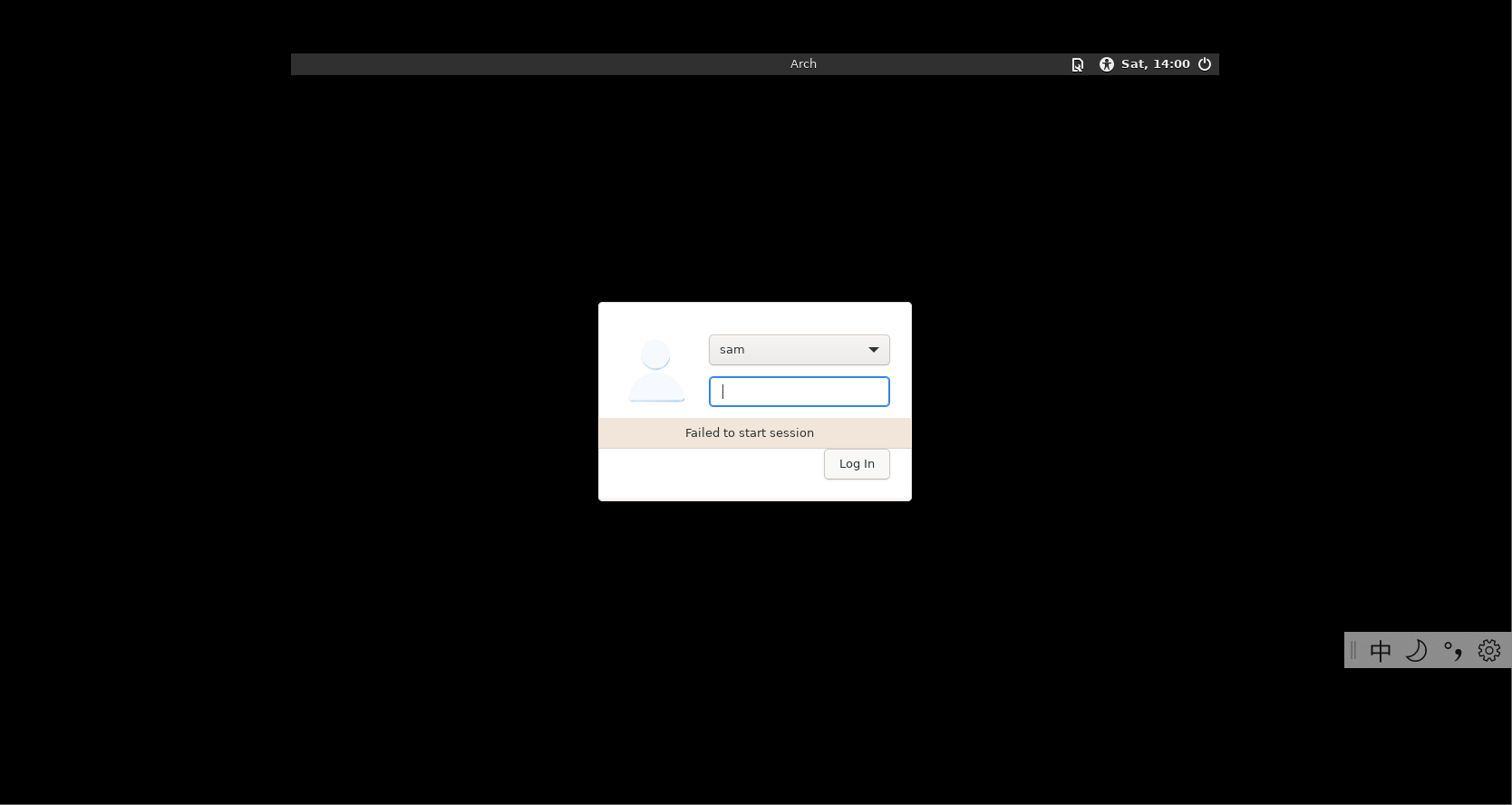
- » 安装完xfce4后无法登录
页次: 1
#1 2021-06-26 14:05:23
- 小钧翊
- 会员

- 注册时间: 2021-05-23
- 帖子: 37
- 个人网站
离线
#2 2021-06-26 14:32:22
- 依云
- 会员

- 所在地: a.k.a. 百合仙子
- 注册时间: 2011-08-21
- 帖子: 8,961
- 个人网站
Re: 安装完xfce4后无法登录
登录失败之后执行 sudo journalctl -n 200 看看最近的日志。
在线
#3 2021-06-26 14:55:58
- 小钧翊
- 会员

- 注册时间: 2021-05-23
- 帖子: 37
- 个人网站
Re: 安装完xfce4后无法登录
依云 说:
登录失败之后执行 sudo journalctl -n 200 看看最近的日志。
有亿些多
login as: sam
sam@192.168.220.134's password:
Last login: Sat Jun 26 14:53:55 2021 from 192.168.220.1
[sam@Arch ~]$ sudo journalctl -n 200
[sudo] password for sam:
-- Journal begins at Sat 2021-06-26 12:57:10 CST, ends at Sat 2021-06-26 14:54:>
Jun 26 14:51:23 Arch kernel: audit: type=1131 audit(1624690283.780:48): pid=1 u>
Jun 26 14:51:25 Arch audit[495]: USER_AUTH pid=495 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:25 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:51:25 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:51:25 Arch lightdm[495]: pam_systemd_home(lightdm:account): systemd-h>
Jun 26 14:51:25 Arch audit[495]: USER_ACCT pid=495 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:25 Arch kernel: audit: type=1100 audit(1624690285.290:49): pid=495>
Jun 26 14:51:25 Arch kernel: audit: type=1101 audit(1624690285.290:50): pid=495>
Jun 26 14:51:25 Arch lightdm[495]: Error getting user list from org.freedesktop>
Jun 26 14:51:25 Arch dhcpcd[394]: ens33: no IPv6 Routers available
Jun 26 14:51:28 Arch systemd[1]: Started Getty on tty2.
Jun 26 14:51:28 Arch audit[1]: SERVICE_START pid=1 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:28 Arch kernel: audit: type=1130 audit(1624690288.233:51): pid=1 u>
Jun 26 14:51:32 Arch audit[504]: USER_AUTH pid=504 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:32 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:51:32 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:51:32 Arch login[504]: pam_systemd_home(login:account): systemd-homed>
Jun 26 14:51:32 Arch audit[504]: USER_ACCT pid=504 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:32 Arch kernel: audit: type=1100 audit(1624690292.487:52): pid=504>
Jun 26 14:51:32 Arch kernel: audit: type=1101 audit(1624690292.487:53): pid=504>
Jun 26 14:51:32 Arch audit[504]: CRED_ACQ pid=504 uid=0 auid=4294967295 ses=429>
Jun 26 14:51:32 Arch audit[504]: SYSCALL arch=c000003e syscall=1 success=yes ex>
Jun 26 14:51:32 Arch audit: PROCTITLE proctitle=2F62696E2F6C6F67696E002D70002D2D
Jun 26 14:51:32 Arch login[504]: pam_unix(login:session): session opened for us>
Jun 26 14:51:32 Arch kernel: audit: type=1103 audit(1624690292.490:54): pid=504>
Jun 26 14:51:32 Arch kernel: audit: type=1006 audit(1624690292.490:55): pid=504>
Jun 26 14:51:32 Arch kernel: audit: type=1300 audit(1624690292.490:55): arch=c0>
Jun 26 14:51:32 Arch kernel: audit: type=1327 audit(1624690292.490:55): proctit>
Jun 26 14:51:32 Arch systemd[1]: Created slice User Slice of UID 1000.
Jun 26 14:51:32 Arch systemd[1]: Starting User Runtime Directory /run/user/1000>
Jun 26 14:51:32 Arch systemd-logind[397]: New session 2 of user sam.
Jun 26 14:51:32 Arch systemd[1]: Finished User Runtime Directory /run/user/1000.
Jun 26 14:51:32 Arch audit[1]: SERVICE_START pid=1 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:32 Arch kernel: audit: type=1130 audit(1624690292.503:56): pid=1 u>
Jun 26 14:51:32 Arch systemd[1]: Starting User Manager for UID 1000...
Jun 26 14:51:32 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:51:32 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:51:32 Arch systemd[506]: pam_systemd_home(systemd-user:account): syst>
Jun 26 14:51:32 Arch audit[506]: USER_ACCT pid=506 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:32 Arch audit[506]: CRED_ACQ pid=506 uid=0 auid=4294967295 ses=429>
Jun 26 14:51:32 Arch audit[506]: SYSCALL arch=c000003e syscall=1 success=yes ex>
Jun 26 14:51:32 Arch audit: PROCTITLE proctitle="(systemd)"
Jun 26 14:51:32 Arch systemd[506]: pam_warn(systemd-user:setcred): function=[pa>
Jun 26 14:51:32 Arch systemd[506]: pam_unix(systemd-user:session): session open>
Jun 26 14:51:32 Arch systemd[506]: pam_env(systemd-user:session): deprecated re>
Jun 26 14:51:32 Arch audit[506]: USER_START pid=506 uid=0 auid=1000 ses=3 msg='>
Jun 26 14:51:32 Arch kernel: audit: type=1101 audit(1624690292.513:57): pid=506>
Jun 26 14:51:32 Arch kernel: audit: type=1103 audit(1624690292.513:58): pid=506>
Jun 26 14:51:32 Arch kernel: audit: type=1006 audit(1624690292.513:59): pid=506>
Jun 26 14:51:32 Arch audit: BPF prog-id=24 op=LOAD
Jun 26 14:51:32 Arch audit[506]: SYSCALL arch=c000003e syscall=321 success=yes >
Jun 26 14:51:32 Arch audit: PROCTITLE proctitle="(systemd)"
Jun 26 14:51:32 Arch audit: BPF prog-id=24 op=UNLOAD
Jun 26 14:51:32 Arch systemd[506]: Queued start job for default target Main Use>
Jun 26 14:51:32 Arch audit[1]: SERVICE_START pid=1 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:32 Arch audit[504]: USER_START pid=504 uid=0 auid=1000 ses=2 msg='>
Jun 26 14:51:32 Arch audit[504]: CRED_REFR pid=504 uid=0 auid=1000 ses=2 msg='o>
Jun 26 14:51:32 Arch systemd[506]: Created slice User Application Slice.
Jun 26 14:51:32 Arch login[504]: pam_env(login:session): deprecated reading of >
Jun 26 14:51:32 Arch systemd[506]: Reached target Paths.
Jun 26 14:51:32 Arch login[504]: LOGIN ON tty2 BY sam
Jun 26 14:51:32 Arch systemd[506]: Reached target Timers.
Jun 26 14:51:32 Arch systemd[506]: Starting D-Bus User Message Bus Socket.
Jun 26 14:51:32 Arch systemd[506]: Listening on GnuPG network certificate manag>
Jun 26 14:51:32 Arch systemd[506]: Listening on GnuPG cryptographic agent and p>
Jun 26 14:51:32 Arch systemd[506]: Listening on GnuPG cryptographic agent and p>
Jun 26 14:51:32 Arch systemd[506]: Listening on GnuPG cryptographic agent (ssh->
Jun 26 14:51:32 Arch systemd[506]: Listening on GnuPG cryptographic agent and p>
Jun 26 14:51:32 Arch systemd[506]: Listening on p11-kit server.
Jun 26 14:51:32 Arch systemd[506]: Listening on D-Bus User Message Bus Socket.
Jun 26 14:51:32 Arch systemd[506]: Reached target Sockets.
Jun 26 14:51:32 Arch systemd[506]: Reached target Basic System.
Jun 26 14:51:32 Arch systemd[506]: Reached target Main User Target.
Jun 26 14:51:32 Arch systemd[506]: Startup finished in 58ms.
Jun 26 14:51:32 Arch systemd[1]: Started User Manager for UID 1000.
Jun 26 14:51:32 Arch systemd[1]: Started Session 2 of user sam.
Jun 26 14:51:42 Arch audit[1]: SERVICE_STOP pid=1 uid=0 auid=4294967295 ses=429>
Jun 26 14:51:42 Arch systemd[1]: systemd-hostnamed.service: Deactivated success>
Jun 26 14:51:42 Arch kernel: kauditd_printk_skb: 10 callbacks suppressed
Jun 26 14:51:42 Arch kernel: audit: type=1131 audit(1624690302.570:66): pid=1 u>
Jun 26 14:51:42 Arch audit: BPF prog-id=22 op=UNLOAD
Jun 26 14:51:42 Arch audit: BPF prog-id=21 op=UNLOAD
Jun 26 14:51:42 Arch audit: BPF prog-id=20 op=UNLOAD
Jun 26 14:51:42 Arch kernel: audit: type=1334 audit(1624690302.663:67): prog-id>
Jun 26 14:51:42 Arch kernel: audit: type=1334 audit(1624690302.663:68): prog-id>
Jun 26 14:51:42 Arch kernel: audit: type=1334 audit(1624690302.663:69): prog-id>
Jun 26 14:51:58 Arch audit[520]: USER_AUTH pid=520 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:58 Arch kernel: audit: type=1100 audit(1624690318.653:70): pid=520>
Jun 26 14:51:58 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:51:58 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:51:58 Arch sshd[520]: pam_systemd_home(sshd:account): systemd-homed i>
Jun 26 14:51:58 Arch audit[520]: USER_ACCT pid=520 uid=0 auid=4294967295 ses=42>
Jun 26 14:51:58 Arch sshd[520]: Accepted password for sam from 192.168.220.1 po>
Jun 26 14:51:58 Arch kernel: audit: type=1101 audit(1624690318.660:71): pid=520>
Jun 26 14:51:58 Arch audit[520]: CRED_ACQ pid=520 uid=0 auid=4294967295 ses=429>
Jun 26 14:51:58 Arch audit[520]: SYSCALL arch=c000003e syscall=1 success=yes ex>
Jun 26 14:51:58 Arch audit: PROCTITLE proctitle=737368643A2073616D205B707269765D
Jun 26 14:51:58 Arch sshd[520]: pam_unix(sshd:session): session opened for user>
Jun 26 14:51:58 Arch kernel: audit: type=1103 audit(1624690318.673:72): pid=520>
Jun 26 14:51:58 Arch kernel: audit: type=1006 audit(1624690318.673:73): pid=520>
Jun 26 14:51:58 Arch kernel: audit: type=1300 audit(1624690318.673:73): arch=c0>
Jun 26 14:51:58 Arch kernel: audit: type=1327 audit(1624690318.673:73): proctit>
Jun 26 14:51:58 Arch systemd[1]: Started Session 4 of user sam.
Jun 26 14:51:58 Arch systemd-logind[397]: New session 4 of user sam.
Jun 26 14:51:58 Arch sshd[520]: pam_env(sshd:session): deprecated reading of us>
Jun 26 14:51:58 Arch audit[520]: USER_START pid=520 uid=0 auid=1000 ses=4 msg='>
Jun 26 14:51:58 Arch audit[522]: CRED_ACQ pid=522 uid=0 auid=1000 ses=4 msg='op>
Jun 26 14:51:58 Arch kernel: audit: type=1105 audit(1624690318.680:74): pid=520>
Jun 26 14:51:58 Arch kernel: audit: type=1103 audit(1624690318.683:75): pid=522>
Jun 26 14:52:03 Arch audit[525]: USER_AUTH pid=525 uid=1000 auid=1000 ses=4 msg>
Jun 26 14:52:03 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:52:03 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:52:03 Arch sudo[525]: pam_systemd_home(sudo:account): systemd-homed i>
Jun 26 14:52:03 Arch kernel: audit: type=1100 audit(1624690323.360:76): pid=525>
Jun 26 14:52:03 Arch kernel: audit: type=1101 audit(1624690323.363:77): pid=525>
Jun 26 14:52:03 Arch audit[525]: USER_ACCT pid=525 uid=1000 auid=1000 ses=4 msg>
Jun 26 14:52:03 Arch audit[525]: CRED_REFR pid=525 uid=1000 auid=1000 ses=4 msg>
Jun 26 14:52:03 Arch audit[525]: USER_START pid=525 uid=1000 auid=1000 ses=4 ms>
Jun 26 14:52:03 Arch sudo[525]: sam : TTY=pts/0 ; PWD=/home/sam ; USER=roo>
Jun 26 14:52:03 Arch sudo[525]: pam_unix(sudo:session): session opened for user>
Jun 26 14:52:47 Arch sudo[525]: pam_unix(sudo:session): session closed for user>
Jun 26 14:52:47 Arch audit[525]: USER_END pid=525 uid=1000 auid=1000 ses=4 msg=>
Jun 26 14:52:47 Arch audit[525]: CRED_DISP pid=525 uid=1000 auid=1000 ses=4 msg>
Jun 26 14:52:47 Arch kernel: kauditd_printk_skb: 2 callbacks suppressed
Jun 26 14:52:47 Arch kernel: audit: type=1106 audit(1624690367.883:80): pid=525>
Jun 26 14:52:47 Arch kernel: audit: type=1104 audit(1624690367.883:81): pid=525>
Jun 26 14:53:00 Arch login[530]: FATAL: /dev/pts/0: change permissions failed: >
Jun 26 14:53:40 Arch sshd[520]: pam_unix(sshd:session): session closed for user>
Jun 26 14:53:40 Arch audit[520]: USER_END pid=520 uid=0 auid=1000 ses=4 msg='op>
Jun 26 14:53:40 Arch audit[520]: CRED_DISP pid=520 uid=0 auid=1000 ses=4 msg='o>
Jun 26 14:53:40 Arch kernel: audit: type=1106 audit(1624690420.460:82): pid=520>
Jun 26 14:53:40 Arch kernel: audit: type=1104 audit(1624690420.460:83): pid=520>
Jun 26 14:53:40 Arch systemd[1]: session-4.scope: Deactivated successfully.
Jun 26 14:53:40 Arch systemd-logind[397]: Session 4 logged out. Waiting for pro>
Jun 26 14:53:40 Arch systemd-logind[397]: Removed session 4.
Jun 26 14:53:55 Arch audit[586]: USER_AUTH pid=586 uid=0 auid=4294967295 ses=42>
Jun 26 14:53:55 Arch kernel: audit: type=1100 audit(1624690435.370:84): pid=586>
Jun 26 14:53:55 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:53:55 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:53:55 Arch sshd[586]: pam_systemd_home(sshd:account): systemd-homed i>
Jun 26 14:53:55 Arch audit[586]: USER_ACCT pid=586 uid=0 auid=4294967295 ses=42>
Jun 26 14:53:55 Arch sshd[586]: Accepted password for sam from 192.168.220.1 po>
Jun 26 14:53:55 Arch audit[586]: CRED_ACQ pid=586 uid=0 auid=4294967295 ses=429>
Jun 26 14:53:55 Arch audit[586]: SYSCALL arch=c000003e syscall=1 success=yes ex>
Jun 26 14:53:55 Arch audit: PROCTITLE proctitle=737368643A2073616D205B707269765D
Jun 26 14:53:55 Arch sshd[586]: pam_unix(sshd:session): session opened for user>
Jun 26 14:53:55 Arch kernel: audit: type=1101 audit(1624690435.383:85): pid=586>
Jun 26 14:53:55 Arch kernel: audit: type=1103 audit(1624690435.383:86): pid=586>
Jun 26 14:53:55 Arch kernel: audit: type=1006 audit(1624690435.383:87): pid=586>
Jun 26 14:53:55 Arch kernel: audit: type=1300 audit(1624690435.383:87): arch=c0>
Jun 26 14:53:55 Arch kernel: audit: type=1327 audit(1624690435.383:87): proctit>
Jun 26 14:53:55 Arch systemd-logind[397]: New session 5 of user sam.
Jun 26 14:53:55 Arch systemd[1]: Started Session 5 of user sam.
Jun 26 14:53:55 Arch sshd[586]: pam_env(sshd:session): deprecated reading of us>
Jun 26 14:53:55 Arch audit[586]: USER_START pid=586 uid=0 auid=1000 ses=5 msg='>
Jun 26 14:53:55 Arch kernel: audit: type=1105 audit(1624690435.393:88): pid=586>
Jun 26 14:53:55 Arch audit[588]: CRED_ACQ pid=588 uid=0 auid=1000 ses=5 msg='op>
Jun 26 14:53:55 Arch kernel: audit: type=1103 audit(1624690435.397:89): pid=588>
Jun 26 14:54:01 Arch login[591]: FATAL: /dev/pts/0: change permissions failed: >
Jun 26 14:54:09 Arch sshd[586]: pam_unix(sshd:session): session closed for user>
Jun 26 14:54:09 Arch audit[586]: USER_END pid=586 uid=0 auid=1000 ses=5 msg='op>
Jun 26 14:54:09 Arch audit[586]: CRED_DISP pid=586 uid=0 auid=1000 ses=5 msg='o>
Jun 26 14:54:09 Arch kernel: audit: type=1106 audit(1624690449.390:90): pid=586>
Jun 26 14:54:09 Arch kernel: audit: type=1104 audit(1624690449.390:91): pid=586>
Jun 26 14:54:09 Arch systemd-logind[397]: Session 5 logged out. Waiting for pro>
Jun 26 14:54:09 Arch systemd[1]: session-5.scope: Deactivated successfully.
Jun 26 14:54:09 Arch systemd-logind[397]: Removed session 5.
Jun 26 14:54:19 Arch audit[646]: USER_AUTH pid=646 uid=0 auid=4294967295 ses=42>
Jun 26 14:54:19 Arch kernel: audit: type=1100 audit(1624690459.967:92): pid=646>
Jun 26 14:54:19 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:54:19 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:54:19 Arch sshd[646]: pam_systemd_home(sshd:account): systemd-homed i>
Jun 26 14:54:19 Arch audit[646]: USER_ACCT pid=646 uid=0 auid=4294967295 ses=42>
Jun 26 14:54:19 Arch sshd[646]: Accepted password for sam from 192.168.220.1 po>
Jun 26 14:54:19 Arch kernel: audit: type=1101 audit(1624690459.973:93): pid=646>
Jun 26 14:54:19 Arch audit[646]: CRED_ACQ pid=646 uid=0 auid=4294967295 ses=429>
Jun 26 14:54:19 Arch audit[646]: SYSCALL arch=c000003e syscall=1 success=yes ex>
Jun 26 14:54:19 Arch audit: PROCTITLE proctitle=737368643A2073616D205B707269765D
Jun 26 14:54:19 Arch sshd[646]: pam_unix(sshd:session): session opened for user>
Jun 26 14:54:19 Arch kernel: audit: type=1103 audit(1624690459.977:94): pid=646>
Jun 26 14:54:19 Arch kernel: audit: type=1006 audit(1624690459.977:95): pid=646>
Jun 26 14:54:19 Arch kernel: audit: type=1300 audit(1624690459.977:95): arch=c0>
Jun 26 14:54:19 Arch kernel: audit: type=1327 audit(1624690459.977:95): proctit>
Jun 26 14:54:19 Arch systemd-logind[397]: New session 6 of user sam.
Jun 26 14:54:19 Arch systemd[1]: Started Session 6 of user sam.
Jun 26 14:54:19 Arch sshd[646]: pam_env(sshd:session): deprecated reading of us>
Jun 26 14:54:19 Arch audit[646]: USER_START pid=646 uid=0 auid=1000 ses=6 msg='>
Jun 26 14:54:19 Arch audit[648]: CRED_ACQ pid=648 uid=0 auid=1000 ses=6 msg='op>
Jun 26 14:54:19 Arch kernel: audit: type=1105 audit(1624690459.987:96): pid=646>
Jun 26 14:54:19 Arch kernel: audit: type=1103 audit(1624690459.987:97): pid=648>
Jun 26 14:54:28 Arch audit[651]: USER_AUTH pid=651 uid=1000 auid=1000 ses=6 msg>
Jun 26 14:54:28 Arch kernel: audit: type=1100 audit(1624690468.610:98): pid=651>
Jun 26 14:54:28 Arch dbus-daemon[389]: [system] Activating via systemd: service>
Jun 26 14:54:28 Arch dbus-daemon[389]: [system] Activation via systemd failed f>
Jun 26 14:54:28 Arch sudo[651]: pam_systemd_home(sudo:account): systemd-homed i>
Jun 26 14:54:28 Arch audit[651]: USER_ACCT pid=651 uid=1000 auid=1000 ses=6 msg>
Jun 26 14:54:28 Arch sudo[651]: sam : TTY=pts/0 ; PWD=/home/sam ; USER=roo>
Jun 26 14:54:28 Arch audit[651]: CRED_REFR pid=651 uid=1000 auid=1000 ses=6 msg>
Jun 26 14:54:28 Arch sudo[651]: pam_unix(sudo:session): session opened for user>
Jun 26 14:54:28 Arch audit[651]: USER_START pid=651 uid=1000 auid=1000 ses=6 ms>
lines 179-201/201 (END)离线
#4 2021-06-26 15:14:56
- 依云
- 会员

- 所在地: a.k.a. 百合仙子
- 注册时间: 2011-08-21
- 帖子: 8,961
- 个人网站
Re: 安装完xfce4后无法登录
意思是让你自己看看哪里出错了。
你这直接从终端复制出来的消息都不完整,右边被截断了,也没法看。
在线
#5 2021-07-10 15:15:34
- WeepingDogel
- 狗狗
- 所在地: 狗窝
- 注册时间: 2021-07-10
- 帖子: 7
- 个人网站
Re: 安装完xfce4后无法登录
汪!你执行这个,然后把链接给我们看
sudo journalctl -n 200|curl -F "c=@-" "https://fars.ee/"离线
#6 2021-07-10 17:29:20
- WeepingDogel
- 狗狗
- 所在地: 狗窝
- 注册时间: 2021-07-10
- 帖子: 7
- 个人网站
Re: 安装完xfce4后无法登录
或者你试试在 tty 用 startx 能不能启动?
离线
#7 2021-07-11 15:49:38
- Radiker
- 会员

- 注册时间: 2021-06-25
- 帖子: 9
Re: 安装完xfce4后无法登录
请问同志有解决吗,我也出现了相同的问题.
离线
页次: 1
- 首页
- » 新手园地
- » 安装完xfce4后无法登录